Penetration testing, also referred to as pen testing involves simulating a cyber attack, on a computer system, network, or web application with the aim of uncovering security weaknesses that could be exploited by an attacker. This type of testing is crucial in an organization’s cybersecurity strategy as it plays a role, in preventing data breaches and other cyber incidents. Penetration Testing Companies have there own methods and phases of penetration testing.
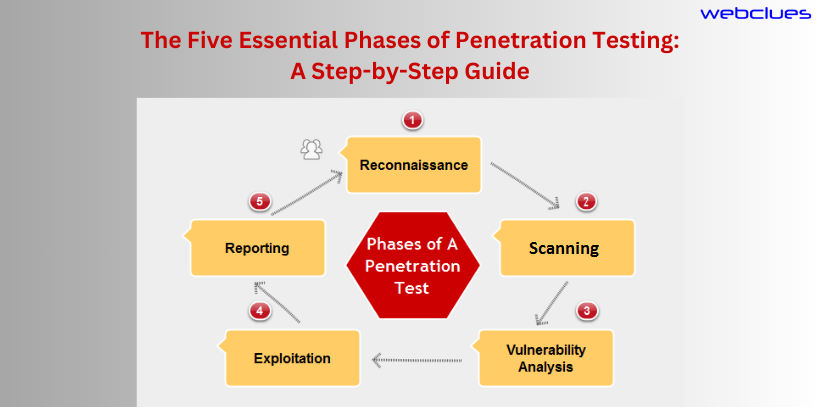
The five essential phases of penetration testing are:
- Reconnaissance:
The initial stage of penetration testing involves acquiring information regarding the target system or network. This can be accomplished through methods, such, as utilizing accessible data employing social engineering techniques, and conducting network scans. - Scanning:
after gathering information the penetration tester will employ scanning tools to identify weaknesses within the target system or network. These scanning tools are capable of detecting an array of vulnerabilities, including known software vulnerabilities, misconfiguration, and easily guessable passwords. - Vulnerability assessment:
During the vulnerability assessment phase the pen tester carefully examines the results to identify which vulnerabilities can be exploited. May pose a threat, to the organization. Additionally, they assign priority levels to these vulnerabilities based on their severity. How easily they can be exploited. - Exploitation:
Once the pen tester has prioritized the vulnerabilities, they will attempt to exploit them to gain access to the target system or network. If successful, the pen tester will be able to demonstrate the impact of the vulnerability and provide recommendations for remediation. - Reporting:
In the final phase of penetration testing, tester will generate a report that summarizes the findings of the test. Provides recommendations for remediation. The report should include a detailed description of each vulnerability, the steps taken to exploit it, and the impact of the vulnerability.
Table of Contents
Step-by-Step Guide to the Five Essential Phases of Penetration Testing
Reconnaissance
The reconnaissance phase is all about gathering as much information as possible about the target system or network. This information can be gathered from a variety of sources, including:
- Publicly available information: Pen testers can gather a lot of information about a target system or network from publicly available sources, such as the target’s website, social media pages, and SERPs.
- Social engineering: Pen testers can also use social engineering techniques to gather information from the target’s employees or customers. For eg, a pen tester might pose as a customer service representative and call the target company to ask about their security procedures.
Scanning
Once the pen tester has gathered enough information about the target system or network, they will use scanning tools to identify potential vulnerabilities.
- Known software vulnerabilities: Scanning tools can identify known software vulnerabilities in the target system’s operating system, applications, and services.
- Misconfigurations: Scanning tools can also identify misconfigurations in the target system’s security settings.
Vulnerability assessment
In the vulnerability assessment phase, the pen tester will analyze the findings from the scanning phase to determine which vulnerabilities are exploitable and pose a risk to the organization. The pen tester will also prioritize the vulnerabilities based on their severity and ease of exploitation.
Exploitation
Once the penetration Testing companies has prioritized the vulnerabilities, they will attempt to exploit them to gain access to the target system or network. If successful, the pen tester will be able to demonstrate the impact of the vulnerability and provide recommendations for remediation.
Reporting
In the final phase of penetration testing, the pen tester will generate a report that summarizes the findings of the test and provides recommendations for remediation. The report should include a detailed description of each vulnerability, the steps taken to exploit it, and the impact of the vulnerability.
WebClues Infotech’s Pen Testing Services
WebClues Infotech is one of the leading Penetration Testing Companies that specializes in providing penetration testing services. The team, at WebClues consists of certified pen testers who can assist you in uncovering and addressing security weaknesses in your systems, networks, and web applications. With a range of penetration testing services available, including Web Application Pentest, API Pentest, Mobile App Pen Testing, External Network Pentest, Internal Network Pentest, Cloud Config Review, etc.. WebClues offers solutions to ensure the security of your assets. If you are looking for a reliable and experienced penetration testing provider, WebClues Infotech is the right choice for you. WebClues can help you to identify and remediate security vulnerabilities in your systems, networks, and web applications, and help you to improve your overall security posture.